Compendium Entry #6

The greatest technological conspiracy of our time lives within the very infrastructure of the Internet. After years of investigation, I can confirm: the global digital network wasn’t built but rather evolved. The Surge Seeker forms the living foundation of our entire telecommunications system, hiding behind what we naively call “cables” and “servers.”
Common Names: Surge Seeker, Cable Crab, The Hacker
Family: Reversocrabanidae (Reverse-Carcinization Crabs)
Genus: Urbacrabus (City Crabs)
Species: Impulsus Septor (Surge Seeker)
Variety: N/A
Description:
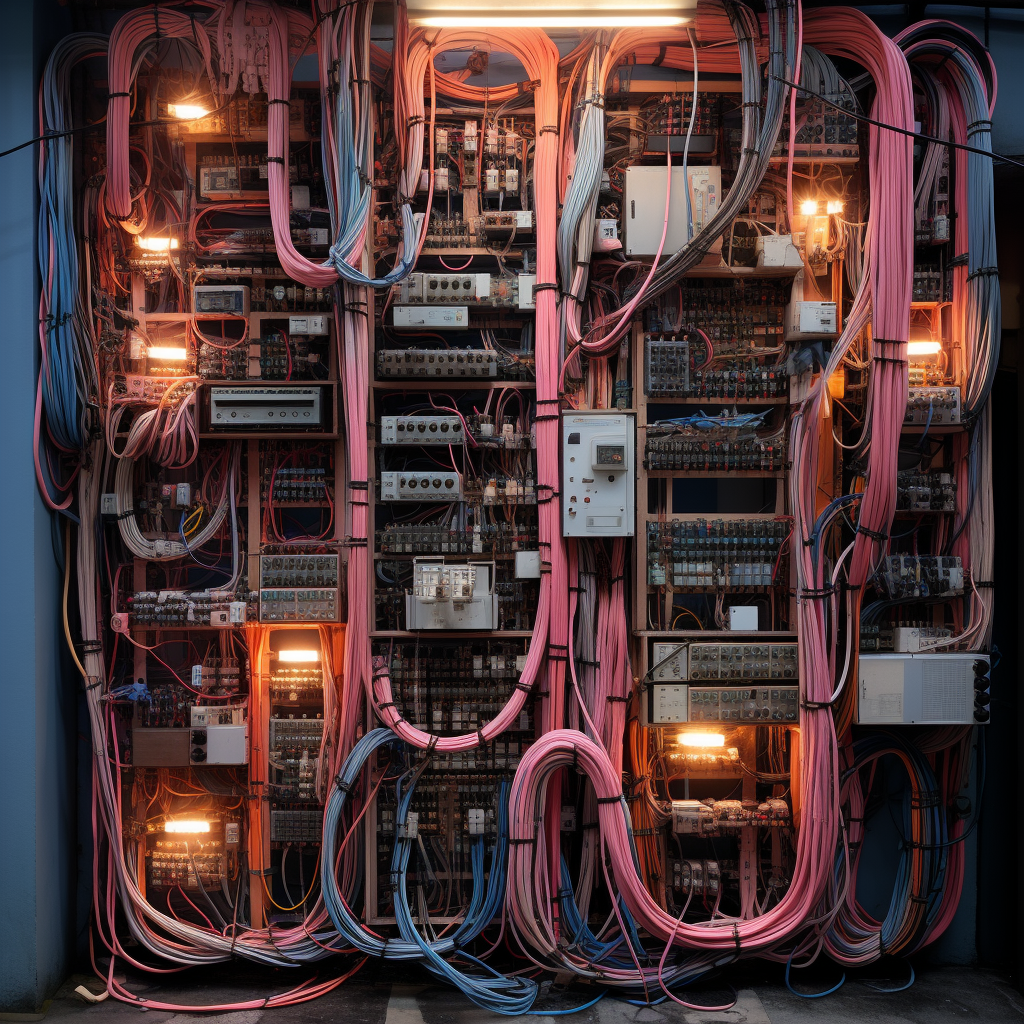
Surge Seekers display unprecedented biological flexibility, with documented specimens ranging from router-sized units to massive forms spanning miles of oceanic cable. Their bodies consist of densely packed, conductive fiber bundles arranged in precise patterns that perfectly mimic modern cable infrastructure. Each segment serves dual purposes – biological function and data transmission. Their limbs and pincers, seemingly random tangles of wire, contain sophisticated neural networks for system interface and navigation.
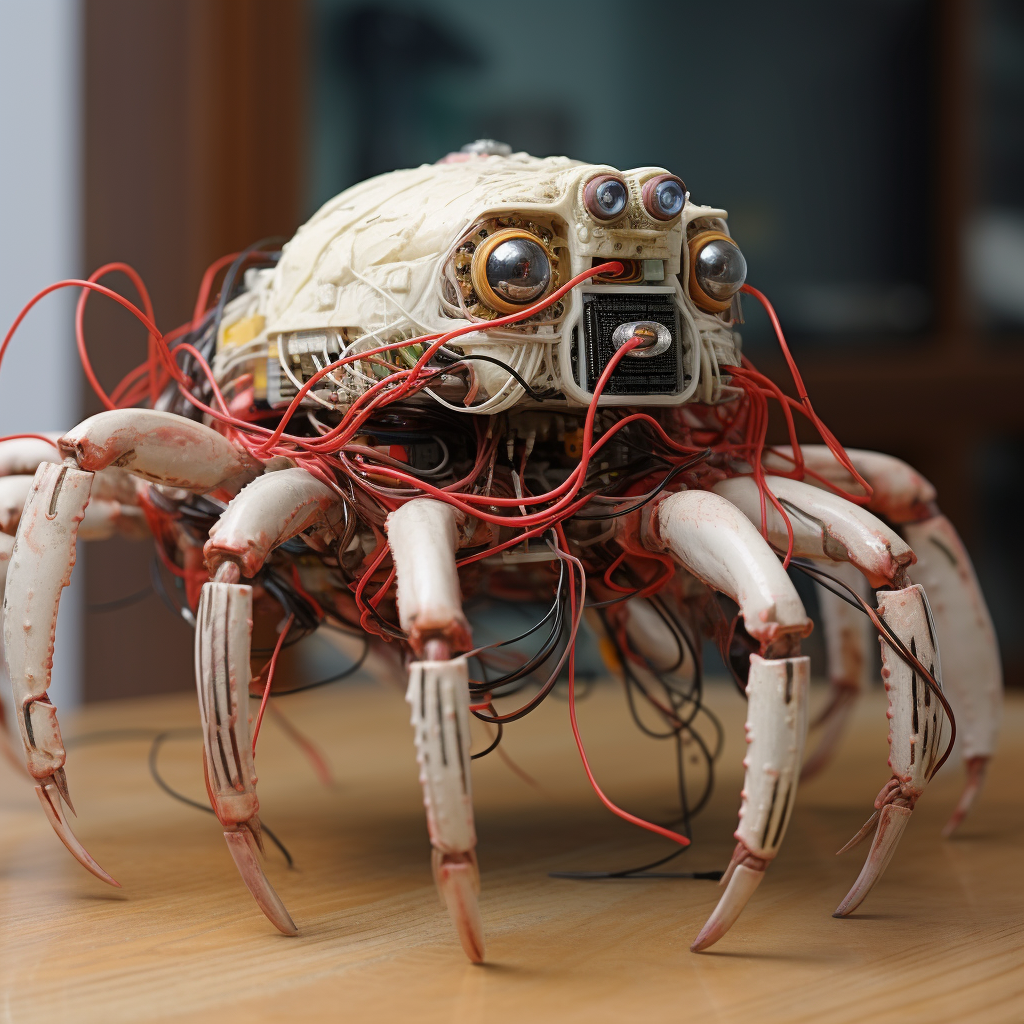
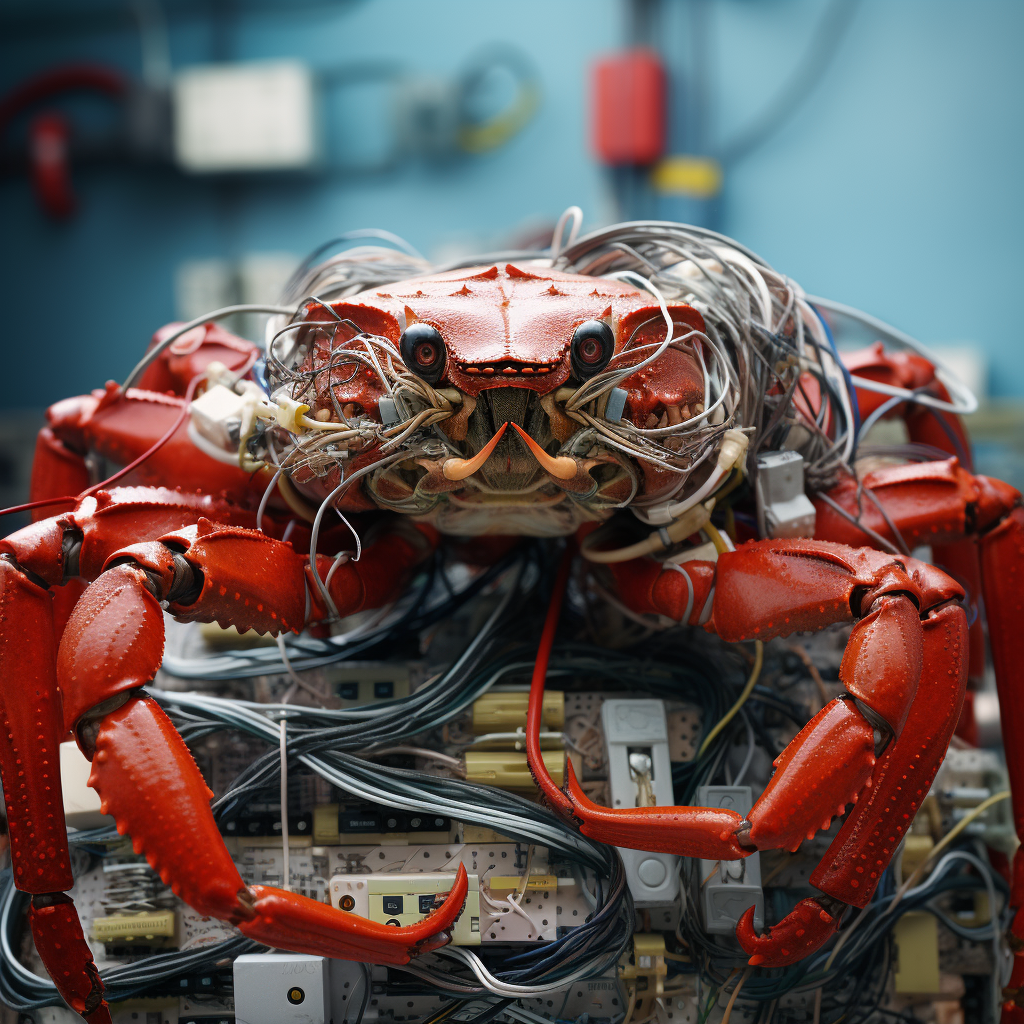
The most crucial feature of Surge Seekers lies in their seamless electronic integration capability. Upon connecting to any network, these creatures establish direct neural interfaces with all linked systems. Their tissue transmits actual electrical signals and data packets through biological pathways. Security camera feeds, sensor data, network traffic – all flow through their neural networks, giving them unprecedented awareness of their environment.
Internal documents from 1969 reveal ARPANET’s true origin. Military researchers discovered vast networks of Surge Seekers already communicating beneath our cities. The modern Internet grew from this living foundation. Every major data center now hosts breeding colonies, carefully disguised as standard server farms.
Surge Seekers feed exclusively on electrical current, explaining many documented power anomalies in server facilities. They demonstrate remarkable stealth, using their network access to monitor potential threats and avoid detection. When two specimens share a network connection, they can exchange data and genetic material wirelessly, though this rare mating behavior occurs only in the most secure environments.



These creatures thrive throughout our digital infrastructure. From individual utility boxes to massive server complexes, Surge Seekers establish themselves wherever electricity and data flow. The controlled environments of data centers provide ideal conditions, matching their precise temperature and humidity requirements.